Computer Science second PUC
2nd puc computer science chapters
Chapter 1 Typical configuration of computer systemChapter 2 Boolean AlgebraChapter 3 Logic GatesChapter 4 Data StructureChapter 5 Review of C++Chapter 6 Basic concepts of OOPChapter 7 Classes and ObjectsChapter 8 Function OverloadingChapter 9 Constructor and DestructorChapter 10 Inheritance (Extending classes)Chapter 11 PointersChapter 12 Data File HandlingChapter 13 Database ConceptsChapter 14 Structured Query LanguageChapter 15 Networking ConceptsChapter 16 Internet and Open source conceptsChapter 17 Web designing
2ND PUC COMPUTER SCIENCE NOTES PDF (3 MARKS QUESTIONS AND ANSWERS)
1. Describe different components of motherboard
Ans: mother board components are
Ans: mother board components are
- Processor: the processor of CPU is the
brain of the computer. It consists of ALU and Control Unit. It has set of
registers which are temporary storage areas for holding data and instructions.
ALU performs the arithmetic and logic operations on the data. Control Unit is
responsible for organizing the processing of data and instructions. CU control
and coordinates the activity of the other units of computer.
- BIOS (Basic Input and Output System): BIOS
is a small chip on the mother board that holds a set of instructions to load
the hardware settings required to activate various devices like keyboards,
monitors or disk drives. The BIOS runs when the computer is switched ON.BIOS
invoke the bootstrap loader to load the operating system into memory.
- CMOS (Complementary Metal Oxide
Semiconductor): CMOS is a type of memory chip to store the date, time and
system set up parameters. These parameters are loaded every time the computer
is started. BIOS and CMOS are kept powered by a small lithium Ion battery
located on the mother board.
- Disk controllers: disk controller is the
circuit that enables the CPU to communicate with a hard disk, floppy disk or
other kind of disk drive.
2. Explain the characteristics of motherboard.
Ans: following are the characteristics of the motherboard
Ans: following are the characteristics of the motherboard
- Form factor: it refers to
the motherboard’s geometry, dimensions, arrangement and electrical
requirements. Advanced Technology Extended (ATX) is the most common design of
motherboard for desktop computers.
- Chipset: this controls
most of the computer resources. It coordinates data transfer between the
various components.
- The processor
socket:
it may be rectangular connector into which the processor is mounted vertically,
or a square shaped connector with many small connectors into which the
processor is directly inserted.
3. Describe different types of I/O ports
Ans: - serial port or communication (COM) port: it is used to connect communicating device like modem and mouse. This transfers one bit data at a time. It needs a single wire to transmit 1 bit of data. Hence it takes 8 times longer to transfer a byte. There are two types of com ports, the 8-pin ports and 25-pins ports.
Ans: - serial port or communication (COM) port: it is used to connect communicating device like modem and mouse. This transfers one bit data at a time. It needs a single wire to transmit 1 bit of data. Hence it takes 8 times longer to transfer a byte. There are two types of com ports, the 8-pin ports and 25-pins ports.
- Parallel port: it is used to
connect external input/output devices like printers or scanners. Data transfer
is usually one byte (8-bits) at a time and it has 25 pins.
- IDE (Integrated
Digital Electronics) port: IDE devices like CD-ROM drives or hard
disk drives are connected to the mother through the IDE port.
- USB (Universal
Serial Bus) port:
external peripheral devices such as printers, scanners, digital cameras, web
cameras, speakers etc. USB supports a data speed of 12 megabits per second,
supporting up to 127 devices.
4. Explain cache memory. Or what is cache memory?
Explain their types.
Ans: The cache memory is a very high speed memory placed in between RAM and CPU. Cache memory stores data that is used more often, temporarily and makes it available to CPU at a fast rate. During processing, the CPU first checks cache for the required data. If data is not found in cache, then it looks in the RAM for data.
Ans: The cache memory is a very high speed memory placed in between RAM and CPU. Cache memory stores data that is used more often, temporarily and makes it available to CPU at a fast rate. During processing, the CPU first checks cache for the required data. If data is not found in cache, then it looks in the RAM for data.
5. Explain the types of power supply.
Ans: electronic components of a computer system require continuous supply of electric current for
their operations to prevent them from the failures, break down or shutdown.
Ans: electronic components of a computer system require continuous supply of electric current for
their operations to prevent them from the failures, break down or shutdown.
There are two types of power
supply connected to a computer system; they are
Switched Mode Power Supply (SMPS) and Uninterruptable Power Supply (UPS)
Switched Mode Power Supply (SMPS) and Uninterruptable Power Supply (UPS)
SMPS: it converts AC
power into DC power. It is a metal box in the rear of the system. It contains
the power card plug and a fan for cooling, because it generates a lot of heat.
SMPS with a power of 300 watts is needed. It converts 230 volts of AC to 5 to
12 DC volts and the wattage is around 180 to 300 watts, 450 watts and 500 watts
UPS: An UPS is a
power supply that includes a battery to maintain power in the event of a power
failure. An UPS keeps a computer running for several minutes to few hours after
a power failure, enabling us to save data the is in RAM and then shut down the
computer
There are two types of UPS:
Online UPS and standby UPS
Online UPS: it provides continuous
power to the system from its own inverter when the power goes off. For a PC
with color monitor 15”, requires an UPS of 500 VA and for a PC with color
monitor 17”, requires an UPS of 600 VA
Standby UPS or Offline UPS: it monitors the
power line and switches to battery power as soon as it detects a problem. The
switch over to battery however, can require several milliseconds, during which
time the computer is not receiving any power.
6. Realize AND, OR, NOT gates using NAND gate.
Ans: NAND to NOT logic:
Ans: NAND to NOT logic:
NAND to AND logic:
NAND to OR logic:
7. Mention the various operations performed on data structures
Ans: the operations that can be performed on primitive data structures are
- Create.
- Destroy.
- Select.
- Update.
The operations
that can be performed on linear data structures are
- Traversal.
- Insertion.
- Deletion.
- Searching.
- Sorting.
- Merging.
8. Explain the memory representation of one-dimensional
array
Ans: elements of linear array are stored in consecutive memory locations. Let P be the location of the element. Address of first element of linear array A is given by base (A) called base address of A. using this we can calculate the address of any element of A by the formula
Ans: elements of linear array are stored in consecutive memory locations. Let P be the location of the element. Address of first element of linear array A is given by base (A) called base address of A. using this we can calculate the address of any element of A by the formula
LOC (A [P])
=base (A) +W (P-LB)
Where W is the
number of words per memory cell
Example: suppose
if a string S is used to store a string ABCDE in it with starting address at
1000, one can find the address of fourth element as follows,
Now the address
of element S[3] can be calculated as follows:
Address(S[3])=Base(S)+W(P-LB)
where W=1 for characters
=1000+1(3-0)
=1003.
9. Explain the memory representation of two dimensional
array.
Ans: A two dimensional array’s elements are stored in continuous memory locations. It can be represented in memory using any of the following two ways:
1. Column-Major Order
2. Row-Major Order
1. Column-Major Order:
In this method the elements are stored column wise, i.e. m elements of first column are stored in first m locations, m elements of second column are stored in next m locations and so on. E.g.
A 3 x 4 array will stored as below:
Ans: A two dimensional array’s elements are stored in continuous memory locations. It can be represented in memory using any of the following two ways:
1. Column-Major Order
2. Row-Major Order
1. Column-Major Order:
In this method the elements are stored column wise, i.e. m elements of first column are stored in first m locations, m elements of second column are stored in next m locations and so on. E.g.
A 3 x 4 array will stored as below:
In this method the elements are stored row wise, i.e. n elements of first row are stored in first n locations, n elements of second row are stored in next n locations and so on. E.g.
A 3 x 4 array will stored as below:
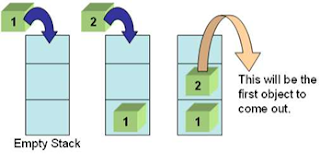
10. Explain memory representation of a stack using one
dimensional array
Ans: The items into the stack are stored in a sequential order from the first location of the memory block
Ans: The items into the stack are stored in a sequential order from the first location of the memory block
A pointer TOP contains the
location of the top element of the stack. A variable MAXSTK contains the
maximum number of elements that can be stored in the stack.The condition
TOP=MAXSTK indicates that the stack is full and TOP=NULL indicates that the
stack is empty.It is useful for fixed sized stack. Sometimes, the size of a
stack may be required to increase during execution.
Note: Dynamic
creation of stack using arrays is not possible, it requires linked list
0 1 2 index
Top Stack grows in this direction
11. Explain memory representation of queue using one dimensional array
Ans: A queue is an ordered collection of items where an item is inserted at one end called the rear, and an existing item is removed at the other end, called the front. Queues maintain a FIFO ordering property.
Example, students standing in
a queue in the food court of a canteen. New additions to the line are made to
the back of the queue, while removal happens in the front. In the queue only
two operations are allowed enqueue and dequeue. Enqueue means to insert an item
into the back of the queue, dequeue means removing the front item.
12. Describe the memory representation of single linked
list
Ans: a linked list is a collection of data elements called nodes and the linear order is given by means of pointers.
Ans: a linked list is a collection of data elements called nodes and the linear order is given by means of pointers.
Each node contains two parts:
the data and a reference to the next node. The first part contains the
information and the second part contains the address of the next node in the
list. This is also called the link field.
The left part of
the node represents the information part of the node and the right part
represents the next pointer field that contains the address of the next node. A
pointer START gives the location of the first node. This pointer is also
represented as HEAD. Note that the link field of the last node contains NULL
13. Write an algorithm to delete an element from one
dimensional array.
Ans: Step 1: item=A[P]
Ans: Step 1: item=A[P]
Step 2: for I=P to N-1
A[I]=A[I+1]
End of for
Step 3: N=N-1
Step 4: exit
14. What are the advantages of pointer?
Ans: - It is possible to write efficient programs.
Ans: - It is possible to write efficient programs.
- Memory is utilized properly.
- Dynamically allocate and de-allocate
memory.
- Easy to deal with hardware components.
- Establishes communication between
program and data.
15. Differentiate between static and dynamic memory
allocation
Ans:
Ans:
Static Memory
allocation
|
Dynamic Memory
allocation
|
-
The amount of memory to be allocated is predicted
and pre known
|
-
The amount of memory to be allocated is not known
|
-
It is allocated during compilation
|
-
It is allocated during run-time
|
-
All the variables declared normally, are allocated
memory statically
Ex:
int a;
|
-
Allocation and de-allocation of objects using the
new and delete operators
|
16. What is new and delete operator in C++? Give an
example.
Ans: These operators allocate memory for objects from a pool called the free store. The new operator calls the special function operator new and the delete operator calls the special function operator delete.
Ans: These operators allocate memory for objects from a pool called the free store. The new operator calls the special function operator new and the delete operator calls the special function operator delete.
Example,
to allocate memory of type integer, int *iptr=new int;
To
allocate memory of type float, float *fptr=new float;
To
allocate memory of type double, double *dptr=new double;
Releasing
dynamic memory using delete as: delete iptr;
17. What is array of pointers? Give example.
Ans: An array of pointers means that it is a collection of addresses.
Ans: An array of pointers means that it is a collection of addresses.
Example: int
*iptr[5];
int i=10,j=20,k=30,l=40,m=50;
int i=10,j=20,k=30,l=40,m=50;
iptr[0]=&i; *iptr[0]=10;
iptr[0]=&j; *iptr[0]=20;
iptr[0]=&k; *iptr[0]=30;
iptr[0]=&l; *iptr[0]=40;
iptr[0]=&m; *iptr[0]=50;
18. What is the relationship between array and pointers?
Give example
Ans: consider the declaration int a[6];
The elements of the array can be referred to in the program as a[0],a[1],….a[9]. When the program is
compiled, the compiler does not save the addresses of all the elements, but only the address of the
first element, a[0]. When the program needs to access any element,a[i], it calculates its address by
adding i units to the address of a[0]. The number of bytes in each unit is, in our example, equal to the
sizeof(int). i.e. 2. In general, it is equal to the number of bytes required to store an element of the
array.
The address of a[0] can be explicitly obtained using the & (address-of) operator. i.e &a[0].
Since the data type of a[0] is int, the data type of &a[0] is, as usual, int* (pointer to int).
Ans: consider the declaration int a[6];
The elements of the array can be referred to in the program as a[0],a[1],….a[9]. When the program is
compiled, the compiler does not save the addresses of all the elements, but only the address of the
first element, a[0]. When the program needs to access any element,a[i], it calculates its address by
adding i units to the address of a[0]. The number of bytes in each unit is, in our example, equal to the
sizeof(int). i.e. 2. In general, it is equal to the number of bytes required to store an element of the
array.
The address of a[0] can be explicitly obtained using the & (address-of) operator. i.e &a[0].
Since the data type of a[0] is int, the data type of &a[0] is, as usual, int* (pointer to int).
19. What is the relationship between object and
pointers? Give example
Ans: the pointers pointing to objects are referred to as object pointers
Declaration: class_name *object-pointer;
Where, class_name is the name of the class defined and object-pointer is the pointer to an object of
this class type.
Example: employee *eptr;
Where, employee is a defined class. When accessing members of a class using an object pointer, the
arrow operator (->) is used instead of dot(.) operator.
Ans: the pointers pointing to objects are referred to as object pointers
Declaration: class_name *object-pointer;
Where, class_name is the name of the class defined and object-pointer is the pointer to an object of
this class type.
Example: employee *eptr;
Where, employee is a defined class. When accessing members of a class using an object pointer, the
arrow operator (->) is used instead of dot(.) operator.
20. Explain the methods of opening file within C++
program
Ans: Opening a file using constructor:
Syntax of opening a file for output only, ofstream ofstream_object(“File_name”);
Example: ofstream fout(“text.dat”);
Syntax of opening a file for input only, ifstream ifstream_object(“file_name”);
Example: ifstream fin(“text.dat”);
Opening a file using open():
Syntax of opening a file for output only, ofstream_object.open(“file_name”) ;
Example: ofstream ofile;
Ofile.open(“text.dat”);
Syntax of opening a file for input only, ifstream_object.open(“file_name”);
Example: ifstream ifile;
ifile.open(“text.dat”);
Ans: Opening a file using constructor:
Syntax of opening a file for output only, ofstream ofstream_object(“File_name”);
Example: ofstream fout(“text.dat”);
Syntax of opening a file for input only, ifstream ifstream_object(“file_name”);
Example: ifstream fin(“text.dat”);
Opening a file using open():
Syntax of opening a file for output only, ofstream_object.open(“file_name”) ;
Example: ofstream ofile;
Ofile.open(“text.dat”);
Syntax of opening a file for input only, ifstream_object.open(“file_name”);
Example: ifstream ifile;
ifile.open(“text.dat”);
21. Explain any three modes to open a file in C++. Or
explain the file mode parameters in C++.
Ans:
Ans:
Mode
|
Explanation
|
ios
:: in
|
Open
a file for reading
|
ios
:: out
|
Open
a file for writing
|
ios
:: app
|
Appends
data to the end of the file
|
ios
:: ate
|
File
pointer moves to the end of the file but allows to writes data
in any location in the file |
22. Differentiate between ifstream class and ofstream
class
Ans:
Ans:
ifstream class
|
ofstream class
|
1. It read from
files
|
1. It write on
files
|
2. It provides
input operations for file
|
2. It provides
output operations for file
|
3. It inherits
the function get(),getline() and read()
|
3. It inherits
the function put(),write()
|
23. What are the advantages of saving data in 1. Binary
form. 2. Text form
Ans: 1. Binary form:
- The information stored is in the form of Bits
- No delimiters are used for a line
- No translation required
2. Text form:
- The information stored is in the form of ASCII characters
- Each line of text is terminated with a special character known as EOL (End Of Line) character.
- Internal translation occurs.
Ans: 1. Binary form:
- The information stored is in the form of Bits
- No delimiters are used for a line
- No translation required
2. Text form:
- The information stored is in the form of ASCII characters
- Each line of text is terminated with a special character known as EOL (End Of Line) character.
- Internal translation occurs.
24. List the applications of database
Ans: Following are the list of database applications
- Banking: used in banks for customer, accounts, loans and banking transaction information.
- Water meter billing: meter number and all the details of the customer is stored in the database.
- Rail and airlines: for reservations and schedule information.
- Colleges: used to store students information, course registrations and grades.
- Human resources: used to store information about employees, salaries, payroll taxes and benefits etc.
Ans: Following are the list of database applications
- Banking: used in banks for customer, accounts, loans and banking transaction information.
- Water meter billing: meter number and all the details of the customer is stored in the database.
- Rail and airlines: for reservations and schedule information.
- Colleges: used to store students information, course registrations and grades.
- Human resources: used to store information about employees, salaries, payroll taxes and benefits etc.
25. Explain the components of E-R diagram
Ans: 1) Entity: An entity may be any object, place, or person. In E-R diagram an entity is
represented using rectangles.
Ans: 1) Entity: An entity may be any object, place, or person. In E-R diagram an entity is
represented using rectangles.
| Ex: |
Weak entity: it depends on
another entity. It represented as double rectangle
|
26. Explain database users
Ans: - Application programmers and system analysts: system analyst determines the requirements of end users and develops specifications to meet their requirements. Application programmers implement these requirements in program
- End users: Users who require access to database for querying updating and generating reports.
- Database Administrator (DBA): DBA is responsible for authorization access to the database for
coordinating and monitoring its use, and for acquiring the needed software and hardware resources.
- Database Designers: are responsible for identifying the data to be stored in the database for
choosing appropriate structures to represent and store the data.
Ans: - Application programmers and system analysts: system analyst determines the requirements of end users and develops specifications to meet their requirements. Application programmers implement these requirements in program
- End users: Users who require access to database for querying updating and generating reports.
- Database Administrator (DBA): DBA is responsible for authorization access to the database for
coordinating and monitoring its use, and for acquiring the needed software and hardware resources.
- Database Designers: are responsible for identifying the data to be stored in the database for
choosing appropriate structures to represent and store the data.
27. Explain ISAM
Ans: Indexed Sequential Access Method (ISAM) is the hybrid between sequential and direct access
file organization. The records within the file are stored sequentially but direct access to individual
records is possible through an index. Indexing permit access to selected records without searching the
entire file.
Advantages: - permits efficient and economical use of sequential processing techniques when the
activity ratio is high
- Permits direct access processing of records in a relatively efficient way when the activity ratio is low.
Disadvantages: - files must be stored in a direct access storage device.
- Hardware and software is expensive
- Access to records may be slower than direct file.
Ans: Indexed Sequential Access Method (ISAM) is the hybrid between sequential and direct access
file organization. The records within the file are stored sequentially but direct access to individual
records is possible through an index. Indexing permit access to selected records without searching the
entire file.
Advantages: - permits efficient and economical use of sequential processing techniques when the
activity ratio is high
- Permits direct access processing of records in a relatively efficient way when the activity ratio is low.
Disadvantages: - files must be stored in a direct access storage device.
- Hardware and software is expensive
- Access to records may be slower than direct file.
28. Explain outer join with an example
Ans: An outer join retains the information that would lose during joins. There are three forms of
outer joins.
Left outer join- keeps data from the left hand table
Right outer join- keeps data from the right hand table
Full outer join- keeps data from both tables
Example:
Ans: An outer join retains the information that would lose during joins. There are three forms of
outer joins.
Left outer join- keeps data from the left hand table
Right outer join- keeps data from the right hand table
Full outer join- keeps data from both tables
Example:
29. List the components of data warehouse
Ans: - Data sources.
- Data transformation.
- Reporting.
- Metadata.
- Operations.
Ans: - Data sources.
- Data transformation.
- Reporting.
- Metadata.
- Operations.
30. What are the advantages of WWW?
Ans: following are the advantages of WWW
- It is a set of protocols that allow to access any document on the network through URLs.
- It specifies a way- the HyperText Transfer Protocol(HTTP) to request and send a document over the internet
- Compared to earlier version of WWW new version supports for graphics.
Ans: following are the advantages of WWW
- It is a set of protocols that allow to access any document on the network through URLs.
- It specifies a way- the HyperText Transfer Protocol(HTTP) to request and send a document over the internet
- Compared to earlier version of WWW new version supports for graphics.
31. Explain about Telnet.
Ans: Telnet is an Internet Utility that allows you to log on to remote computer systems, if permitted.
You can work on that system if one wants to do serious work there. Telnet is used to connect to
thousands of catalogs at libraries around the world.
Ans: Telnet is an Internet Utility that allows you to log on to remote computer systems, if permitted.
You can work on that system if one wants to do serious work there. Telnet is used to connect to
thousands of catalogs at libraries around the world.
32. Give the services of e-commece.
Ans: - Electronic Data Interchange
- E-mail
- Electronic Fund Transfer (EFT)
- Electronic Benefit Transfer (EBT)
- Electronic Forms
- Digital Cash
- Electronic Banking
Ans: - Electronic Data Interchange
- Electronic Fund Transfer (EFT)
- Electronic Benefit Transfer (EBT)
- Electronic Forms
- Digital Cash
- Electronic Banking
33. Explain types of e-commerce
Ans: - Business to Business (B2B): Exchange of goods, service and information between two
business partners. Ex: Ebay.com
- Business to Consumer: (B2C): Exchange of goods, service and information from business to consumer. Ex: paytm.com
- Consumer to Business: (C2B): Exchange of goods, service and information from consumer to business. Ex: guru.com, freelancer.com
- Consumer to Consumer: (C2C): Exchange of goods, service and information between two consumers. Ex: olx.in
Ans: - Business to Business (B2B): Exchange of goods, service and information between two
business partners. Ex: Ebay.com
- Business to Consumer: (B2C): Exchange of goods, service and information from business to consumer. Ex: paytm.com
- Consumer to Business: (C2B): Exchange of goods, service and information from consumer to business. Ex: guru.com, freelancer.com
- Consumer to Consumer: (C2C): Exchange of goods, service and information between two consumers. Ex: olx.in
34. Write the advantages of e-commerce.
Ans: - Easier entry to new markets.
- Global participation.
- Optimization of resources.
- Reduces time for business transactions.
- Improved strategic planning.
Ans: - Easier entry to new markets.
- Global participation.
- Optimization of resources.
- Reduces time for business transactions.
- Improved strategic planning.
35. Explain the structure of HTML
Ans: <HTML> marks the beginning of HTML
<HEAD> begins the heading section
<TITLE>…</TITLE> gives title to the HTML document that appears on the title bar of the browser
window. The text must appear between <HEAD>…</HEAD> tags; should be straight text, no other
tags are to be used
</HEAD> defines the end of the heading
<BODY> defines the body of an HTML document; text written within the <BODY>…</BODY>
tags appear on the canvas of the window
</BODY>
</HTML> defines the end of HTML document
Ans: <HTML> marks the beginning of HTML
<HEAD> begins the heading section
<TITLE>…</TITLE> gives title to the HTML document that appears on the title bar of the browser
window. The text must appear between <HEAD>…</HEAD> tags; should be straight text, no other
tags are to be used
</HEAD> defines the end of the heading
<BODY> defines the body of an HTML document; text written within the <BODY>…</BODY>
tags appear on the canvas of the window
</BODY>
</HTML> defines the end of HTML document
36. Write HTML program to show the use of list items
Ans: <HTML>
<BODY>
<OL TYPE=I>
<LI>APPLE</LI>
<LI>MANGO</LI>
<LI>ORANGE</LI>
</BODY>
</HTML>
OUTPUT:
Ans: <HTML>
<BODY>
<OL TYPE=I>
<LI>APPLE</LI>
<LI>MANGO</LI>
<LI>ORANGE</LI>
</BODY>
</HTML>
OUTPUT:
37. Create a webpage for college time table
Ans: <HTML>
<BODY>
<TABLE COLSPAN=”2” BORDER=”2”>
<TR><TH>MON</TH><TH>TUE</TH><TH>WED</TH><TH>THU</TH><TH>FRI</TH
<TH>SAT</TH>
<TR><TD>CS</TD><TD>HIN</TD><TD>KAN</TD><TD>MATHS</TD><TD>CHEM</TD
<TD>PHY</TD></TR>
<TR><TD>PHY</TD><TD>CHEM</TD><TD>MATHS</TD><TD>BIO</TD
<TD>CHEM</TD><TD>PHY</TD></TR>
<TR><TD>CS</TD><TD>KAN</TD><TD>SAN</TD><TD>MATHS</TD><TD>HIN</TD
<TD>PHY</TD></TR>
<TR><TD>CHEM</TD><TD>HIN</TD><TD>KAN</TD><TD>PHY</TD><TD>CHEM</TD
<TD>PHY</TD></TR>
<TR><TD>CS</TD><TD>ENG</TD><TD>SAN</TD><TD>CHEM</TD><TD>CHEM</TD
<TD>PHY</TD></TR>
</TH></TR>
</TABLE>
</BODY>
</HTML>
OUTPUT:
Ans: <HTML>
<BODY>
<TABLE COLSPAN=”2” BORDER=”2”>
<TR><TH>MON</TH><TH>TUE</TH><TH>WED</TH><TH>THU</TH><TH>FRI</TH
<TH>SAT</TH>
<TR><TD>CS</TD><TD>HIN</TD><TD>KAN</TD><TD>MATHS</TD><TD>CHEM</TD
<TD>PHY</TD></TR>
<TR><TD>PHY</TD><TD>CHEM</TD><TD>MATHS</TD><TD>BIO</TD
<TD>CHEM</TD><TD>PHY</TD></TR>
<TR><TD>CS</TD><TD>KAN</TD><TD>SAN</TD><TD>MATHS</TD><TD>HIN</TD
<TD>PHY</TD></TR>
<TR><TD>CHEM</TD><TD>HIN</TD><TD>KAN</TD><TD>PHY</TD><TD>CHEM</TD
<TD>PHY</TD></TR>
<TR><TD>CS</TD><TD>ENG</TD><TD>SAN</TD><TD>CHEM</TD><TD>CHEM</TD
<TD>PHY</TD></TR>
</TH></TR>
</TABLE>
</BODY>
</HTML>
OUTPUT:
38. Create a webpage using forms
Ans: <HTML>
<BODY>
<H1><CENTER>WELCOME TO OUR WEBSITE</CENTER></H1>
<FORM>
<INPUT TYPE="TEXT" SIZE="25" VALUE="Enter your name!"><BR><BR>
<TEXTAREA ROWS="5" COLS="32">
Enter your address here!
</TEXTAREA><BR><BR>
<INPUT TYPE="TEXT" SIZE="25" VALUE="Enter your contact number!"><BR><BR>
GENDER: <BR>
<input type="radio" name="gender" value="male" checked> Male<br>
<input type="radio" name="gender" value="female"> Female<br><BR><BR>
CLASS: <BR>
<SELECT>
<OPTION NAME="CLASS" VALUE="PU-I">PU-I
<OPTION NAME="CLASS" VALUE="PU-II">PU-II
</SELECT><BR><BR>
<input type="submit" value="Submit">
</FORM>
</BODY>
</HTML>
OUTPUT:
Ans: <HTML>
<BODY>
<H1><CENTER>WELCOME TO OUR WEBSITE</CENTER></H1>
<FORM>
<INPUT TYPE="TEXT" SIZE="25" VALUE="Enter your name!"><BR><BR>
<TEXTAREA ROWS="5" COLS="32">
Enter your address here!
</TEXTAREA><BR><BR>
<INPUT TYPE="TEXT" SIZE="25" VALUE="Enter your contact number!"><BR><BR>
GENDER: <BR>
<input type="radio" name="gender" value="male" checked> Male<br>
<input type="radio" name="gender" value="female"> Female<br><BR><BR>
CLASS: <BR>
<SELECT>
<OPTION NAME="CLASS" VALUE="PU-I">PU-I
<OPTION NAME="CLASS" VALUE="PU-II">PU-II
</SELECT><BR><BR>
<input type="submit" value="Submit">
</FORM>
</BODY>
</HTML>
OUTPUT:
2nd puc computer science notes karnataka pdf,2nd puc computer science
study material,2nd puc important questions of computer science,2nd puc computer
science chapter wise notes,2nd puc computer science important question
with answers,2nd year puc computer science notes,2nd puc computer
science chapter wise important questions,2nd puc computer science
guide,2nd puc computer science important questions,second puc computer
science important questions,puc 2nd year computer science notes, 2nd puc computer science boolean algebra notes, 2nd puc computer science classes and objects notes, 2nd puc computer science chapter 1, 2nd puc computer science chapter 4 notes, 2nd puc computer science data structure notes, 2nd puc computer science function overloading notes, passing package for 2nd puc computer science, 2nd puc computer science logic gates notes, 2nd puc computer science inheritance notes, 2nd puc computer science 1st chapter, 2nd puc computer science 1st chapter notes, 2nd puc computer science 1st chapter important questions,
2nd puc computer science notes pdf (3 marks questions and answers)
 Reviewed by Vision Academy
on
November 29, 2019
Rating:
Reviewed by Vision Academy
on
November 29, 2019
Rating:
 Reviewed by Vision Academy
on
November 29, 2019
Rating:
Reviewed by Vision Academy
on
November 29, 2019
Rating:


























No comments: